Table of Contents
Alright, degens, builders tuning into the ApexWeb3 frequency. Let’s talk about trust. Or rather, the lack of it online. How many times have you stared at a sketchy DeFi site, wondering if hitting ‘approve’ is gonna drain your wallet faster than a weekend in Vegas? How do we even know that the NFT sitting in your wallet is the real deal, not some cheap knock-off someone copied and pasted? The digital world is slippery. Data gets changed, manipulated, and faked. It’s a mess.
Enter the blockchain. We hear about it being the “trust machine,” the great ledger in the sky that can’t be fudged. But how? What’s the secret sauce preventing some whale or shadowy super-coder from rewriting history and making off with everyone’s bags?
The core question boils down to this: how does a hash help secure blockchain technology? Forget magic internet money for a sec; this is about the fundamental tech making decentralized trust possible. Get this, and you’re way ahead of the curve. We’re gonna break down what is a hash in blockchain, why it’s the MVP of crypto security, and how this simple concept stops the whole thing from collapsing into chaos.
So, What the Heck is Hashing Anyway? The Digital Fingerprint Machine
Forget complex math for a moment. Think of hashing like a hyper-specific, irreversible blender.
- The Analogy: You toss any ingredients (your data – could be a transaction, a picture, the entire text of “War and Peace”) into this magic blender (the hashing algorithm). You hit ‘ON’. Whirr! Out comes a smoothie (the hash) that always looks exactly the same if you used the exact same ingredients in the exact same amounts. Change one strawberry to a raspberry? Totally different smoothie.
- The (Slightly More) Techy Def: Hashing is a process where a mathematical algorithm (like the legendary SHA-256, the bitcoin hashing algorithm workhorse) takes an input of any size and spits out a fixed-size string of characters. This output string is the “hash” or “digest.” It’s a unique digital fingerprint for that specific input data.
Now, why is this “digital fingerprint” such a big deal? Because these blockchain hash functions come with some seriously useful traits:
- Consistent Output: No matter how many times you run the same data through a hash function, you’ll always get the exact same result. No randomness, pure consistency.
- Fast Computation: Calculating a hash from data is quick and easy for computers. No waiting around for ages.
- Pre-Image Resistance (It’s a One-Way Street, Ser): This is HUGE. Given a hash output, it’s practically impossible to figure out what the original input data was. Like trying to un-blend that smoothie back into perfect, separate fruits. Good luck. This prevents someone from reverse-engineering data from its fingerprint.
- Small Change, Big Effect (The Avalanche Effect): Change just one tiny bit in the input data – like a single comma in that novel, or one digit in a transaction amount – and the resulting hash output changes completely and unpredictably. It’s not just slightly different; it’s a whole new fingerprint. This makes tampering instantly obvious.
- Collision Resistance: It’s insanely unlikely (like, finding-a-specific-atom-in-the-universe unlikely with strong algorithms like SHA-256) that two different inputs will accidentally produce the same hash output. If they did, that’s a “collision,” and it would break the system’s integrity. That’s why using strong, battle-tested algorithms matters.
Understanding these properties is critical. They are the bedrock for understanding how does a hash help secure blockchain technology.
Putting the Hash to Work: Securing Blocks & Building the Chain
Okay, we know what is hash in crypto – it’s a unique data fingerprint. Now, how does this actually lock down the blockchain? It works on two main levels:
1. Keeping Data Inside Each Block Honest (Integrity Checksum)
Think of a block like a container holding a batch of recent, confirmed transactions. You don’t want anyone messing with those records after they’re in, right?
- Hashing the Goods: All the transaction data within a block gets hashed. Often, this is done cleverly using something called a Merkle Tree.
- (Quick Merkle Tree Sneak Peek): Picture taking each transaction and hashing it separately. Then, you hash pairs of those hashes together. You keep hashing the pairs upwards until you get one single hash at the top – the “Merkle Root.” It’s like a super-condensed summary hash representing all the transactions below it. Why? It’s super efficient for verifying if a specific transaction is included in the block without needing to check all of them. You can learn more about how nodes use this stuff in our guide on how blockchain nodes work.)
- The Benefit: This Merkle Root (or a simple hash of all block data) acts as a tamper seal for the entire block’s contents. If anyone tries to alter any transaction detail within that block after it’s been created, the Merkle Root hash will change completely (remember the Avalanche Effect?). Instant red flag. The integrity is shot. This verification step plays a crucial role in confirming blockchain transactions.
2. Linking Blocks Together Like Unbreakable Digital Lego (The “Chain”)
This is where the “chain” part of blockchain gets its security superpowers, all thanks to blockchain hashing.
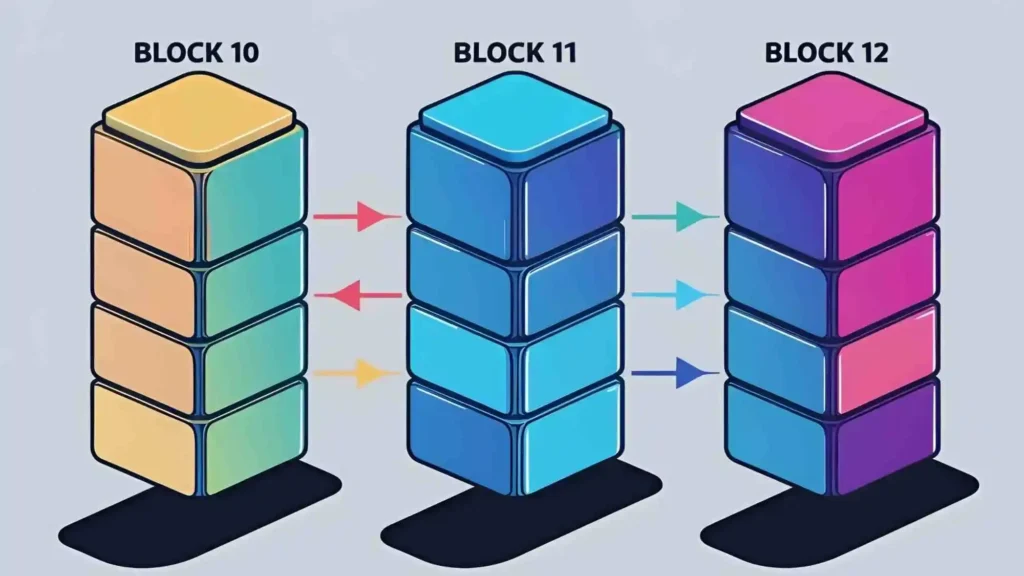
- The Mechanism: Every new block that gets added to the chain doesn’t just contain its own data hash (like the Merkle Root). Most importantly, the block’s header holds the hash of the preceding block.
- The Analogy: Imagine a series of transparent, sealed boxes (blocks). Box #11 not only has a unique seal based on its own contents, but that seal also incorporates the exact seal code from Box #10. Box #12’s seal incorporates Box #11’s seal code, and so on.
- Chain Reaction Consequence: Now, imagine some script kiddie tries to go back and tamper with the data in old Box #10. What happens?
- The data inside Box #10 changes.
- Because the data changed, the unique hash (seal code) of Box #10 changes completely.
- But wait! Box #11’s header contains the original hash of Box #10. Now there’s a mismatch. Box #11 is pointing to a previous hash that no longer exists.
- This mismatch instantly invalidates Box #11. And since Box #12 relies on Box #11’s hash… Box #12 is now also invalid. And Box #13, and #14, all the way to the end of the chain!
3. The Grand Finale: Immutability (Why Rewriting History is NGMI)
Combine these two hashing applications:
- Hashing within blocks protects the integrity of the data inside each block.
- Hashing the previous block’s hash into the current block creates an unbreakable chain linking them together.
Try to tamper with any historical block? You break its internal hash and you break the hash link for every single block that came after it.
An attacker can’t just alter a single block to rewrite history — they’d have to modify every connected block too. They’d need to:
- Alter the data in the target block.
- Recalculate the hash for that altered block.
- Modify the next block to include this new hash.
- Recalculate the hash for that block.
- Repeat this process for every single subsequent block all the way to the present.
- Oh, and they need to do this faster than the entire honest network is adding new blocks. (Good luck beating thousands of decentralized nodes).
- Plus, on chains like Bitcoin using Proof-of-Work, recalculating each block’s hash also involves solving a computationally insane puzzle.
This combination of cryptographic hashing and (usually) decentralization makes tampering computationally infeasible and economically irrational on any reasonably established blockchain. This is the essence of immutability – not that data can’t physically be changed on one computer, but that doing so verifiably breaks the chain and the rest of the network will reject it. It’s tamper-evident by design. Want a deeper dive into the basics? Take a look at our guide: “What is Blockchain and How Does It Work?“
Real-World Feel: The Never-Ending, Self-Auditing Spreadsheet
Think of the blockchain like a massive, shared Google Sheet that everyone can see but (almost) nobody can cheat.
- Rows as Transactions: Each row added is a transaction or piece of data.
- Pages as Blocks: Rows get bundled onto pages (blocks).
- The Magic Checksum (Hashing): At the bottom of each page (block), there’s a unique checksum code (the block’s hash) calculated from all the rows on that page. This checksum isn’t just for the current page — it also incorporates the one before it.
- Tampering Attempt: If someone tries to secretly change a number in a row on Page 50, the checksum for Page 50 instantly changes.
- Obvious Discrepancy: Now, the checksum printed on Page 51 (which was based on the original Page 50 checksum) no longer matches the new checksum of the altered Page 50. The link is broken.
- Public Rejection: Everyone else looking at their copy of this giant spreadsheet instantly sees the discrepancy starting at Page 50/51 and knows that version is corrupted. They stick with the original, untampered chain.
This self-auditing nature, enabled by blockchain hashing, is what creates trust without needing a central referee. Whether it’s a public or private blockchain, this principle remains core.
Beyond the Basics: Hashing Everywhere
Hashing isn’t just about linking blocks. It pops up elsewhere:
- Algorithm Evolution: While SHA-256 is king for Bitcoin, other chains might use different algorithms (like SHA-3, Keccak-256 used by Ethereum). Staying ahead of potential future attacks (like quantum computing, maybe?) means research into stronger blockchain hash functions is always ongoing. Sometimes network upgrades require a blockchain hard fork to implement changes, which can take time to process (how long does a blockchain hard fork take?).
- Proof-of-Work (PoW): In Bitcoin, “mining” is essentially a race where nodes crunch numbers trying to find a specific type of hash (one starting with a certain number of zeros) that includes A block’s hash is generated from its data combined with a random number called a nonce.. Hashing is central to the energy-intensive security model of PoW.
Keepin’ It Real: The Limits & Caveats
Hashing’s powerful, but don’t mistake it for some kind of digital magic trick. Few points to keep in your back pocket:
- Collision Risk (Theoretical AF): While insanely rare for strong algorithms like SHA-256, it’s theoretically possible for two different inputs to produce the same hash. If a practical collision attack were found for SHA-256, it would be a black swan event forcing a massive crypto infrastructure upgrade. Highly unlikely today, but the reason research continues.
- Garbage In, Immutable Garbage Out: Hashing secures data integrity – it proves data hasn’t been tampered with after being added. It does not guarantee the data was accurate or truthful in the first place. If someone records BS onto the blockchain, hashing just ensures it stays BS immutably. DYOR still applies, always.
The TL;DR: Hash = Blockchain Security Bedrock
So, how does a hash help secure blockchain technology? Let’s break it down one last time:
- Data Fingerprint: A hash function produces a unique, fixed-size digital signature for any given data.
- Block Integrity: Hashing data within blocks (often via Merkle Trees) ensures that if any transaction is changed, the block’s overall hash changes, flagging tampering.
- Chain Connection: By storing the previous block’s hash in each new block, the blockchain forms a secure, cryptographic link. Altering one block will disrupt the entire chain moving forward.
- Immutability: This chaining makes altering past data computationally infeasible and economically irrational on a decentralized network, leading to tamper-evidence and immutability.
Understanding what is hash in crypto and its role through blockchain hashing isn’t just academic; it’s fundamental to grasping why this tech offers a different paradigm for digital trust. It’s the cryptographic glue holding the whole decentralized dream together.
Now spit your thoughts below. Did this clear things up? What other core tech concepts feel like gatekept alpha? Drop your questions and war stories on Discord, or share this with a friend who still thinks blockchain is just magic.
Frequently Asked Questions (FAQ)
Can you reverse a blockchain hash?
Pretty much no. Cryptographic hash functions like SHA-256 used in blockchain hashing are designed as one-way functions (pre-image resistance). Given a hash, figuring out the original input data is computationally infeasible – basically impossible with current tech.
What happens if someone changes data in an old blockchain block?
Changing data in an old block alters its hash completely (due to the Avalanche Effect). Because each block contains the hash of the previous one, this change breaks the cryptographic link between the tampered block and the next one. This invalidates the tampered block and all subsequent blocks on that altered chain, making the tampering obvious to the rest of the network, which follows the valid, longer chain.
Is SHA-256 the only hash function used in blockchain?
No, while SHA-256 is famous (thanks to being the bitcoin hashing algorithm), it’s not the only one. Ethereum uses Keccak-256 (part of the SHA-3 standard). Different blockchains might use different blockchain hash functions based on their design choices and security considerations.
Does hashing make blockchain 100% secure?
Hashing provides incredibly strong data integrity and tamper-evidence. However, overall blockchain security also depends on the consensus mechanism (PoW, PoS), network decentralization, smart contract security (a whole other beast!), and user-level security (not getting phished!). Hashing is a critical component of security, not the entire picture.





