Table of Contents
Your exchange isn’t just a business—it’s a bank vault with an API. Time to audit the hell out of that contract.
The $69M Lesson That Could’ve Been a $10K Audit
Three months ago, I was sitting in a Discord war room watching panic unfold in real-time. An “established” exchange (let’s call them ExchangeX) had just lost $69 million in user funds. All because they skipped a proper security audit on their new cross-chain bridge feature.
“But we had our smart contracts audited!” the CTO kept repeating.
Yeah, they did—but only the contracts. Not the off-chain infrastructure. Not the wallet architecture. Not the actual implementation of the bridge. Classic security theater that cost users everything.
The brutal truth? A comprehensive security audit for exchanges would have caught the vulnerability in their hot wallet rotation mechanism within hours. Instead, users became exit liquidity for the attacker who decompiled their way to a fortune.
Why Security Audits are Non-Negotiable for Exchanges
Let’s cut the BS: security audits for exchanges aren’t just another compliance checkbox—they’re literally existential. Here’s why you should be auditing like your life depends on it (because your business absolutely does):
Protecting User Funds & Assets
This is the fundamental reason, and it’s not theoretical. In 2022 alone, exchanges lost more than $3 billion in hacks. Each one of those exchanges had some form of “security” in place—just not the right kind.
When KuCoin got ripped for $281 million in 2020, they survived only because of three things:
- They had enough reserves to cover losses
- They had proper incident response procedures (from previous audits)
- They could prove to users they’d fixed the vulnerabilities (with post-hack audits)
Without these elements, they’d have been another dead exchange logo on a PowerPoint about crypto disasters.
Building & Maintaining User Trust
In an industry where “not your keys, not your coins” is gospel, exchanges fight an uphill battle for trust. Comprehensive security audits demonstrate that you’re not just another exit scam waiting to happen.
When Kraken publishes their Proof of Reserves with cryptographic verification following their security audits, they’re not just flexing—they’re building the foundation for long-term customer relationships in an industry plagued by rug pulls.
Meeting Regulatory Requirements (Exchange Security Compliance)
The regulatory hammer is coming down worldwide, and exchange security compliance is becoming the price of admission:
- Europe’s MiCA regulations explicitly require “robust systems” and security measures
- Singapore’s Payment Services Act mandates specific technology risk management practices
- US state-by-state frameworks (NY’s BitLicense being the most stringent) require documented security programs
Security audits provide evidence that you’ve implemented these requirements properly. When regulators knock, your audit reports become your best friends.
Investor Due Diligence
Try raising money without security audits. I’ll wait.
Every serious VC firm now has a technical due diligence checklist, and exchange security audits top the list. As one Paradigm partner told me recently: “We don’t even schedule a second meeting until we’ve seen their security audit history.”
Insurance & Banking Relationships
Want insurance against hacks? Try getting coverage without security audits. The premium difference alone will pay for your audit ten times over.
Nexus Mutual and other DeFi insurance protocols explicitly price their premiums based on security audit history. Traditional insurers won’t even quote you without them.
As for banking—good luck establishing fiat on/off ramps without proving your exchange security compliance through formal audits.
Business Continuity & Reputation Management
When (not if) your exchange faces an incident, having a track record of security audits can be the difference between “concerning but handled professionally” and “total loss of confidence.”
Binance survived multiple incidents not just because of their size, but because they could point to their security practices, including regular blockchain security audits and remediation efforts.
Competitive Advantage
Security is becoming a feature, not just a requirement. Exchanges that can demonstrate rigorous security practices through regular security audits for exchanges attract security-conscious users—often the ones with the most valuable portfolios.
Understanding the Scope: What Does an Exchange Security Audit Cover?
A proper exchange security audit is comprehensive AF. If your auditor only wants to look at one aspect of your exchange, they’re not giving you real security—they’re giving you false confidence.
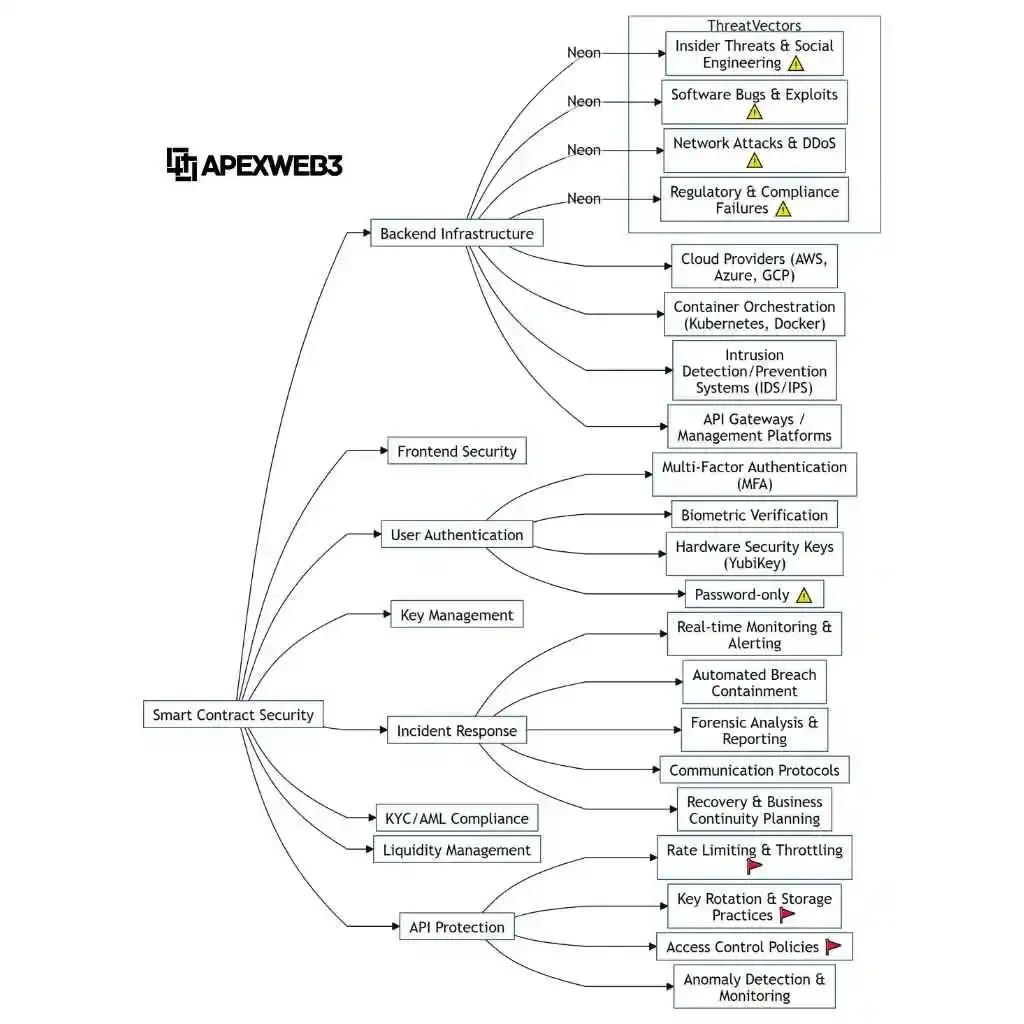
Holistic Approach: It’s All Connected
Exchange security isn’t modular—vulnerabilities in one area cascade into others. A proper blockchain security audit examines how components interact, not just how they function individually.
Key Areas (The Real Deal Breakdown):
Infrastructure Security
- Cloud configuration audits (AWS, GCP, Azure)
- Network security assessment
- Firewall rule reviews and testing
- DDoS mitigation verification
- Server hardening validation
I’ve seen exchanges running critical infrastructure with default AWS security groups. Don’t be that exchange.
Platform/Application Security
- Web application penetration testing (OWASP Top 10)
- API security assessment (auth, rate limiting, input validation)
- Mobile app security testing (iOS/Android)
- Session management review
- Authentication mechanism analysis
Remember when an exchange leaked user data through a simple API parameter manipulation? Their “audit” hadn’t included API fuzzing tests. Classic rookie mistake.
Wallet Architecture & Management
- Hot/cold/warm wallet security review
- Multi-sig implementation verification
- Key generation & storage procedures (HSMs)
- Transaction signing process analysis
- Custody solution assessment
This is where most exchange hacks begin. Your fancy ML trading engine means nothing if your wallet architecture leaks private keys.
Smart Contract Audits
- For exchanges with DeFi features
- Staking contract reviews
- Bridge security assessment
- Custom token implementation audits
The crossover between CEX and DeFi requires specialized defi security audit techniques that many traditional security firms miss entirely.
Blockchain Interaction Security
- Secure node communication verification
- Transaction monitoring systems assessment
- 51% attack mitigation planning
- Consensus mechanism understanding
Your blockchain security audit must verify that you’re interacting with chains correctly—especially when handling multiple chains with different finality models.
Code Review
- Secure coding practice assessment
- Dependency vulnerability scanning
- Logic flaw identification
- Privilege escalation testing
An exchange I advised last year had a critical vulnerability in a Node.js dependency that their “security scans” had missed. A proper code review would have caught it immediately.
Internal Controls & Access Management
- Role-based access control (RBAC) validation
- Employee vetting procedures review
- Privileged access management assessment
- Segregation of duties verification
The Celsius collapse revealed how poor internal controls can be just as devastating as technical vulnerabilities.
Compliance Checks
- KYC/AML implementation verification
- Data privacy controls (GDPR, CCPA)
- Regulatory reporting mechanisms
- Sanctions screening procedures
Your exchange security compliance isn’t just about tech—it’s about processes too.
Incident Response & Disaster Recovery
- IR plan assessment
- Tabletop exercise evaluation
- Backup and recovery testing
- Communication protocols review
When shit hits the fan, you’ll discover if your IR plans are worth the Google Docs they’re written on.
The Exchange Security Audit Process: A Step-by-Step Methodology
Let’s demystify how a proper exchange security audit actually works:
Phase 1: Scoping & Information Gathering
- Defining objectives and scope boundaries
- Asset inventory and classification
- Threat modeling workshop
- Security questionnaires
- Documentation review (policies, procedures, previous assessments)
Pro tip: The quality of your audit is determined here. If your auditor skimps on this phase, they’re setting up to miss critical vulnerabilities.
Phase 2: Automated Scanning & Analysis
- Static Application Security Testing (SAST)
- Dynamic Application Security Testing (DAST)
- Network vulnerability scanning
- Configuration analysis
- Dependency checks
But remember: tools find known issues, not novel attack vectors. This is just the beginning.
Phase 3: Manual Penetration Testing & Vulnerability Validation
- Skilled penetration testers attempting exploitation
- Business logic testing (crucial for exchanges)
- Custom attack scenario execution
- Privilege escalation attempts
- Social engineering simulations
This is where the real value happens. I’ve watched auditors find million-dollar bugs that no scanner could ever detect—by thinking like attackers and understanding exchange operations.
Phase 4: Specific Audits (as needed)
- Code review sessions
- Smart contract analysis
- Cloud configuration deep dives
- Cryptographic implementation verification
For exchanges with unique features, specialized audits target those specific risk areas.
Phase 5: Reporting
- Detailed findings with severity ratings (CVSS)
- Exploitation proof-of-concepts
- Actionable remediation steps
- Executive summary for leadership
- Technical details for engineering team
A good report doesn’t just list vulnerabilities—it explains impact and provides concrete fixes.
Sample Report Structure:
- Executive Summary
- Methodology
- Findings Summary (with risk ratings)
- Detailed Findings
- Remediation Recommendations
- Appendices (technical details, evidence)
Phase 6: Remediation & Re-testing
- Collaborative fix verification
- Regression testing
- Follow-up scanning
- Final security posture assessment
An audit without remediation is just an expensive PDF. The real value is in fixing what’s found.
Types of Security Audits & When You Need Them
Different situations call for different types of blockchain security audits:
Full Scope Audit
When: Before launch, annually thereafter, or after major architecture changes What: Comprehensive review of all security aspects Cost Range: $50,000-$200,000+ depending on complexity Duration: 3-6 weeks
Penetration Test
When: Quarterly or bi-annually What: Simulated attack to identify exploitable vulnerabilities Cost Range: $15,000-$60,000 Duration: 1-3 weeks
Vulnerability Assessment
When: Monthly or continuous What: Identifying and cataloging security weaknesses Cost Range: $5,000-$30,000 per assessment, or subscription-based Duration: 3-10 days
Compliance Audit
When: As required by regulatory frameworks What: Verification of controls required by specific standards (ISO 27001, SOC 2, etc.) Cost Range: $15,000-$100,000+ depending on framework Duration: 2-8 weeks
Delta Audit
When: After significant code or architecture changes What: Focused assessment of changes and their security impact Cost Range: $10,000-$50,000 Duration: 1-2 weeks
Choosing the Right Security Audit Partner
Not all auditors are created equal. Here’s how to separate the real blockchain security audit firms from the charlatans:
Specialization
Look for firms with proven experience auditing crypto exchanges specifically. General web app security firms often miss crypto-specific attack vectors like MEV exploitation, sandwich attacks, or flash loan vulnerabilities.
Methodology & Tools
The right partner uses a blend of automated and manual testing, with transparency about their process. Ask about their approach to exchange-specific threats like transaction signature manipulation or RPC node compromise.
Team Expertise
Verify that the team has:
- Relevant certifications (OSCP, OSCE, etc.)
- Background in blockchain/crypto security
- Experience with exchanges specifically
- Published research on crypto vulnerabilities
Reputation & References
Check for:
- Case studies specific to exchanges
- Public disclosure of vulnerabilities they’ve found
- Testimonials from recognized exchange clients
- Community reputation in security circles
Reporting Quality
Request a sanitized sample report to evaluate:
- Level of detail
- Actionable recommendations
- Technical accuracy
- Clarity of communication
Red Flags to Avoid
- Bargain-basement pricing (you get what you pay for)
- Guarantees of “no findings” (impossible for any real exchange)
- Extremely short timeframes (thorough audits take time)
- No crypto-specific expertise
Beyond the Audit: Continuous Security & Improvement
A security audit for exchanges is not a one-and-done checkbox. It’s the beginning of your security journey:
Remediation is Key
The most important part happens after the audit—fixing the issues found. Prioritize based on risk, not ease of fixing.
Implementing Monitoring
- Security Information and Event Management (SIEM)
- Intrusion Detection/Prevention Systems (IDPS)
- Blockchain transaction monitoring
- Behavior analytics
Trail of Bits found that 87% of exchange compromises showed warning signs that monitoring would have caught.
Bug Bounty Programs
Leverage the community through platforms like:
- Immunefi
- HackerOne
- Bugcrowd
- Self-hosted programs
Bug bounties complement (not replace) formal security audits for exchanges.
Security Culture
- Regular team training
- Security champions program
- Threat intelligence sharing
- Tabletop exercises
OKX requires all developers to complete security training quarterly—and it shows in their code quality.
Regular Re-Audits
Security degrades over time as:
- New threats emerge
- Code changes
- Team members rotate
- Infrastructure evolves
The most secure exchanges audit continuously, not just annually.
Conclusion
Security audits for exchanges aren’t optional—they’re survival. In an industry where a single vulnerability can mean total collapse, comprehensive and regular blockchain security audits are your insurance policy against disaster.
The question isn’t whether you can afford proper exchange security audits. It’s whether you can afford the alternative.
As we’ve seen time and again in this space: you can pay for security now, or you can pay much more later. And by then, it might be too late.
FAQ
How much does an exchange security audit cost?
Comprehensive exchange security audits typically range from $50,000 to $250,000 depending on exchange size, complexity, features, and audit scope. Specialized components like defi security audit modules may add $15,000-$50,000. Remember: if an audit seems surprisingly cheap, they’re probably cutting critical corners.
How long does a proper exchange security audit take?
A thorough security audit for exchanges typically takes 3-6 weeks for the initial assessment, plus 1-2 weeks for remediation verification. Rushed audits miss things—period.
What’s the difference between a penetration test and a full exchange security audit?
A penetration test simulates attacks to find exploitable vulnerabilities but focuses primarily on execution. A thorough blockchain security audit reviews the system’s architecture, codebase, operational workflows, and infrastructure to uncover exploitable issues and deeper security flaws. Think of pentests as testing if your doors are locked; audits check if you have the right doors in the first place.
Is a smart contract audit enough for an exchange?
Absolutely not. Smart contracts represent only a single layer within the broader security framework of a crypto exchange. A proper security audit for exchanges must cover infrastructure, application security, wallet architecture, operational security, and compliance. Exchanges that only audit smart contracts are leaving massive attack surface unexamined.
How often should exchanges undergo security audits?
At minimum:
– Full scope audit: Annually
– Penetration testing: Quarterly
– Vulnerability assessments: Monthly
– Compliance audits: As required by regulations
– Delta audits: After significant changes
High-value targets should consider continuous security testing programs
Can AI replace human auditors for exchange security?
AI-powered platforms such as Code4rena and Sherlock can support human auditors, but they are not a substitute for expert manual reviews. The most critical vulnerabilities in exchanges often involve complex business logic, multi-step attacks, and novel exploitation techniques that current AI tools cannot identify reliably.
Got thoughts? Did this clear things up? What other core tech concepts feel like tightly held alpha? Drop your questions and war stories in our Discord, or pass this along to a friend who still thinks blockchain is just magic internet money.
Check out our related pieces:
- Upgradeable Smart Contracts: The Good, The Bad & The Rekt
- Blockchain Development Hub: Security First Approaches
This article was researched using data from Chainalysis, CertiK alerts, and real-world audit findings from top exchanges. All exploits mentioned occurred on public blockchains and have been previously disclosed.






